About
Abhishek Tiwari is a researcher and engineering leader with deep expertise in software engineering, security and privacy, service-oriented architectures, and large-scale distributed systems. He currently serves as Editor for the Journal of Open Source Software (JOSS) and Journal of Open Research Software (JORS).
Background
As engineering leader, Abhishek has demonstrated competencies across multiple verticals including but not limited to SaaS, E-commerce, Retail, Media, Ad-Tech, MarTech, and Bioinformatics. He played a pivotal role in the development and scaling of several SaaS products and digital platforms with an Annual Run Rate (ARR) of $100M+/year.
He has a proven track record of building, growing, and leading large geographically distributed high-performance engineering, data, and technology teams (up to 100 people) with a strong focus on culture, delivery, and innovation. Abhishek truly enjoys mentoring and coaching managers and individual contributors.
Abhishek offers a delicate balancing act that ensures his teams are staying ahead of the technology curve (streaming pipelines, pub-sub, multi-cloud, microservices, Kubernetes, service mesh, serverless, deep learning, NLP, AI, IoT) while delivering products and business outcomes in a very fast pace environment.
He helps organizations to develop and scale the culture of DevOps, Developer Experience, and continuous delivery which enables them to excel in key indicators of overall software delivery performance. Abhishek has been part of several major successful transformational initiatives and greenfield projects but he also has a fair share of failures.
Abhishek is passionate about building, scaling, and leading high-performance engineering teams with a great focus on culture and innovation. He practices servant leadership and he helps his teams to realise their full potential by creating an environment of trust and safety where everyone takes extreme ownership. Hem is committed to the personal and professional development of individuals in his teams.
Last but not least, Abhishek provides product management, and software engineering leadership to his teams. He is a tireless advocate of diversity in tech, open-source, operational excellence, and continuous improvement. He regularly writes on his blog and speaks at various forums.

Website
This website is about all things technology, product, and engineering leadership. It covers a variety of topics including but not limited to technical architecture, cloud computing, data architecture, software engineering, algorithms, data engineering, big data, machine Learning, artificial intelligence, devops, continuous delivery, microservices, product management, people leadership, etc.
Reach
Every month, over 20,000 software engineers, computer science researchers, technology professionals, and industry practitioners visit this website looking for interesting new findings in their area of interest.
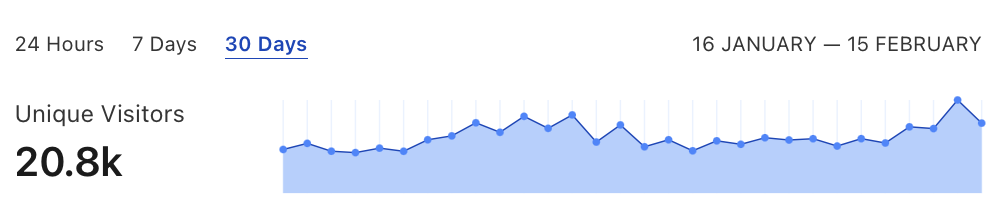
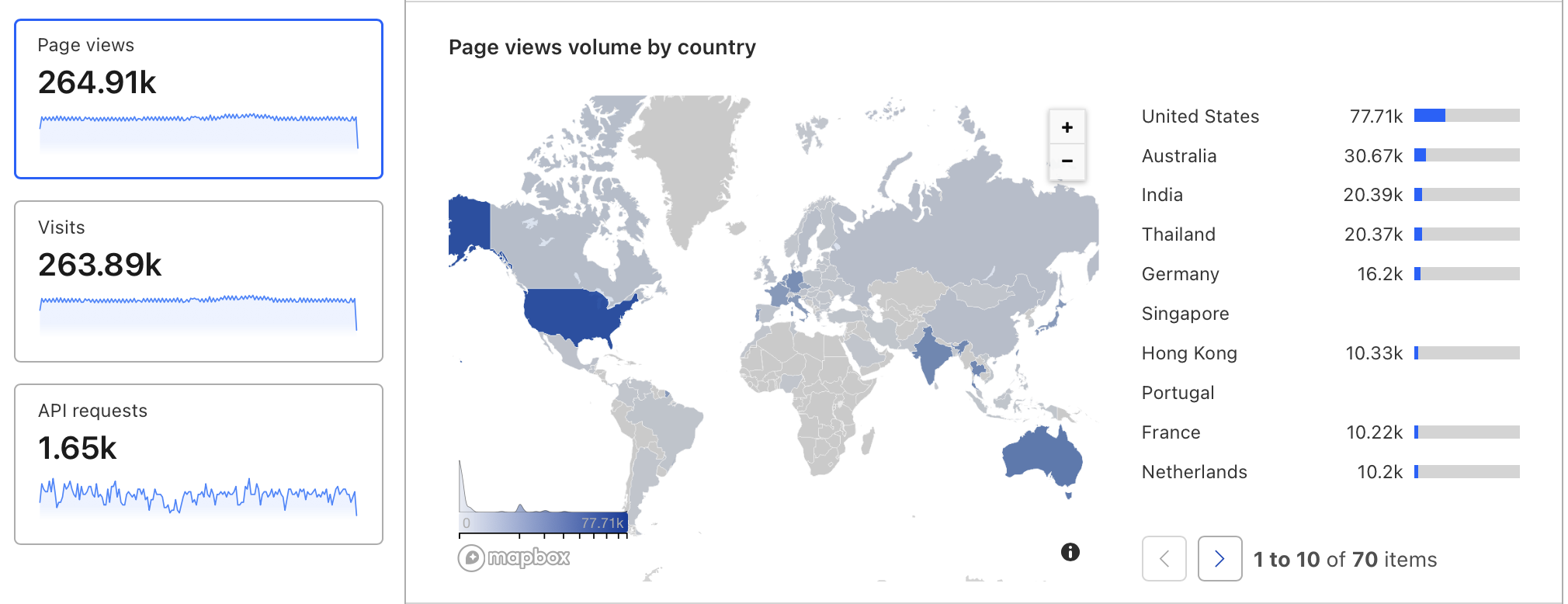
On average we get 250k page views per week or more than 1M page views every month with majority or it coming organically via Google from across the globe.
Research Interests
Network Analysis, Network Visualization, Graph Theory, Data Structures, Developer Productivity, Developer Experience, Systems Biology, Bioinformatics, Cheminformatics, Scientific Computing, Information Security, Information Systems, Workflow Systems, Data Privacy, Confidential Computing, Natural Language Processing (NLP), Machine Learning (ML), Neural Networks, Deep Learning, Data Engineering, Data Pipelines, Distributed Systems, IoT, Sensors, Edge Computing, CDNs, Serverless Computing, Microservices, APIs, FAIR Data, Simulations, Emulations.
Disclosure:
Abhishek currently works for Amazon as a Senior Software Development Manager. At Amazon, he leads the CloudAuth engineering organization in New York.
Colophon
This site is built with Hugo, hosted and served by Cloudflare.
Disclaimer:
This is a personal website and all opinions expressed here are the author’s personal views and not those of his current or previous employers or partners he works or worked with. For questions about this website, please contact Abhishek Tiwari (abhishek at abhishek-tiwari.com).